CrowdStrike IT Incident
Update - Microsoft has released an official recovery tool to support impacted businesses and users.
Over the past 48 hours, we’ve witnessed one of the largest global IT incidents in recent history, caused by a software bug from the security company CrowdStrike.
Microsoft has predicted that 8.5 million Windows systems have been impacted, disrupting commerce, travel, healthcare, manufacturing, advertisement and many more industries.
Specifically, on the 19th of July, as part of ongoing operations, CrowdStrike released a sensor configuration update to Windows systems.
Sensor configuration updates are an ongoing part of the protection mechanisms of the CrowdStrike Falcon platform.
The configuration update triggered a logic error (likely a null pointer exception) resulting in a system crash and blue screen of death (BSOD) on impacted systems, which persists on reboot.
Thankfully, my company was not directly impacted. Therefore, I thought I would explain why.
As part of our enterprise architecture principles, we prioritise vertical integration for endpoint security.
This means, wherever possible, we leverage the native capabilities of the underlying platform (e.g., Windows, Linux, macOS, etc.)
This strategy has three primary benefits:
-
An improved user experience, avoiding the need for multiple third-party software packages that consume resources, impacting performance and reliability.
-
Simplified, lower-cost support, removing the need for IT to procure, manage and lifecycle multiple independent security software packages.
-
Improved security posture, acknowledging that third-party software focused on security commonly requires kernel-level operating system access. Ironically, this makes security software a prime target for cyber-attacks and a continuous software assurance risk.
It is this strategy that protected us from the recent global IT incident.
It would be easy to blame Microsoft for the state of Windows security and they should take partial accountability. However, due to a series of flawed regulatory and legal controls, society must also take responsibility, as it is these controls that have “forced” the use of third-party security software, arguably making the underlying operating system less secure/reliable.
Steven Sinofsky (ex-president of the Windows division at Microsoft) shared the following tweet (which I agree with).
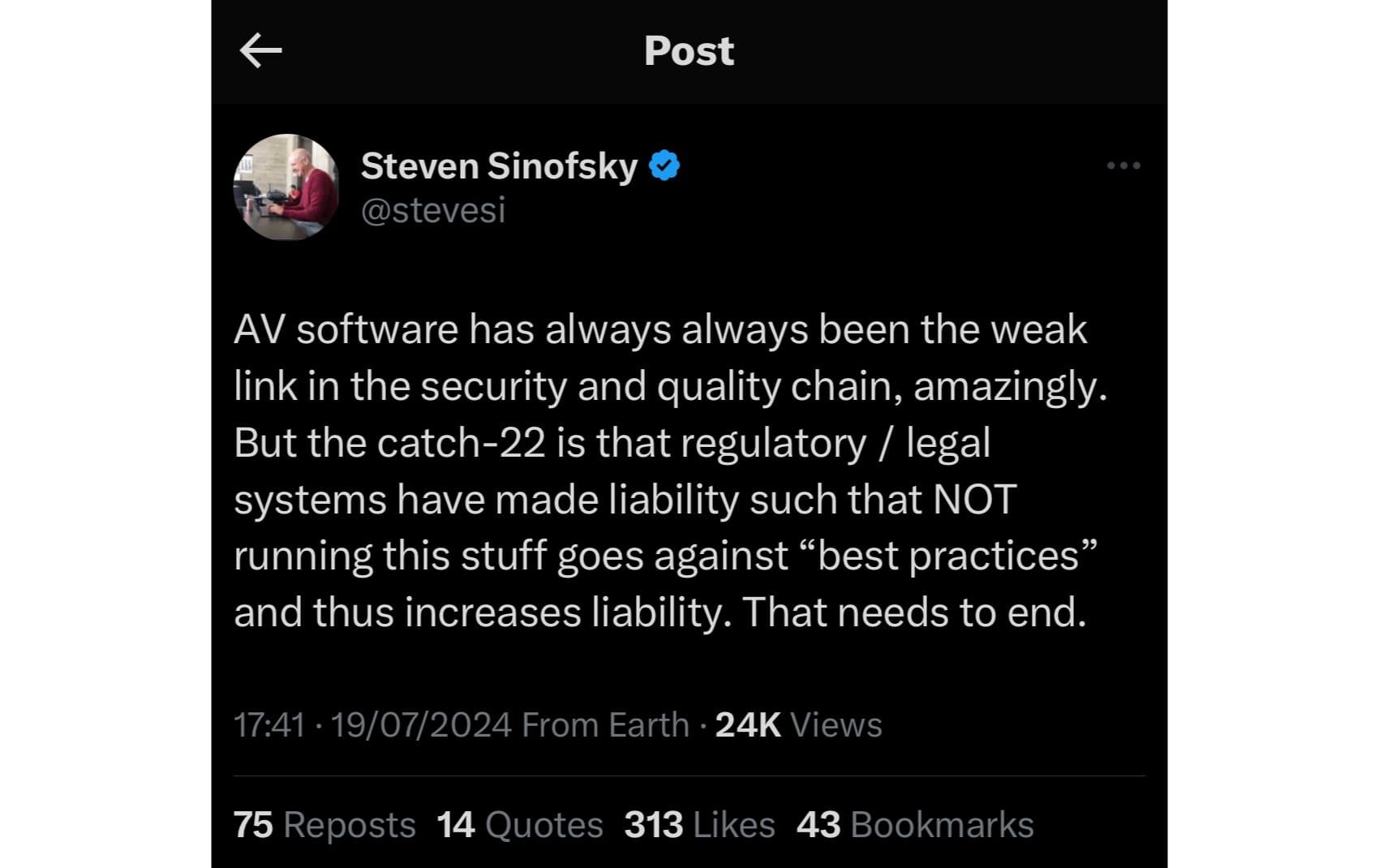
With that said, our strategy is not perfect and like all things, has its trade-offs. Therefore, we must continue to make smart decisions to ensure these trade-offs are understood and/or mitigated via other technologies and/or techniques.
I empathise with the global IT community, who will likely be in the spotlight for days/weeks as they work diligently to recover from this incident.
Finally, this incident is a warning for the IT industry (and the world), highlighting the fragility of the interconnected ecosystem, specifically as it relates to common foundations, such as Microsoft Windows, etc.
If you are impacted by this incident, I recommend reviewing the official CrowdStrike documentation for details regarding the recovery procedure.
As a reminder, cybercriminals will likely attempt to use this incident as a channel of attack. Therefore, only reference and/or engage with official (verified) documentation from CrowdStrike or a trusted partner.